Understanding the zero trust concept in the cloud
Leverage your cybersecurity strategy by implementing the zero trust model.
Palo Alto
As the hacking onslaught continues against all businesses of any size, IT is increasingly turning to the zero trust model to protect their data. By refusing to trust any data source and always verifying identity, zero trust protects a business by segmenting networks, denying the hacker’s favorite tool of lateral movement while simplifying controls for user access.
Security solutions for businesses are evolving fast in the face of new threats delivered at increasing volumes. There is no time for any IT team to monitor the fast-flowing stream of information from cloud services, remote workers and clients or customers, any one of whom could be on a compromised device.
Zero trust turns the traditional concept on its head by assuming that all users and data packets are suspect, within and from outside the business. That assumption stops users or hacker tools freely navigating a network and introducing further breaches.
The zero-trust concept and key principles
The zero-trust concept came to us from Forrester security and risk analyst, and now CTO for Palo Alto Networks, John Kindervag. He identified that by trusting users and their devices, we were increasing risk. By not trusting anyone or anything until they are strongly authenticated, that risk is reduced. The model is a concept, not a set of concrete rules, therefore it is flexible and can be improved as threats change. The approach has been adopted by many network and cloud security providers and represents a strong future for data and network security.
Zero trust works through a set of key principles that can be deployed through a single security app or a set of services to better protect the business, by building trust at every level of a request. These include:
- Build Zero Trust Networks: Creating a single strong source of user identity (the user is who they say they are)
- Use Zero Trust Devices: Ensuring both user and device/machine authentication (they have the rights to access a network through single sign on or multi-factor authentication)
- Create Zero Trust Policies: Adding context to access rights through policy compliance and device health
- Limit Actions Through Zero Trust: Enforcing policies to access an application and data (their actions are limited)
- Use Zero Trust Applications: Enforcing access control policies within an application (managing access rights)
These create a set of rules for any business and their IT security provider to deliver a zero-trust architecture through best practices.
The basics to deploying zero trust
According to John Kindervag and Palo Alto, while zero trust looks simple, there is a set of steps to follow to create a zero-trust environment.
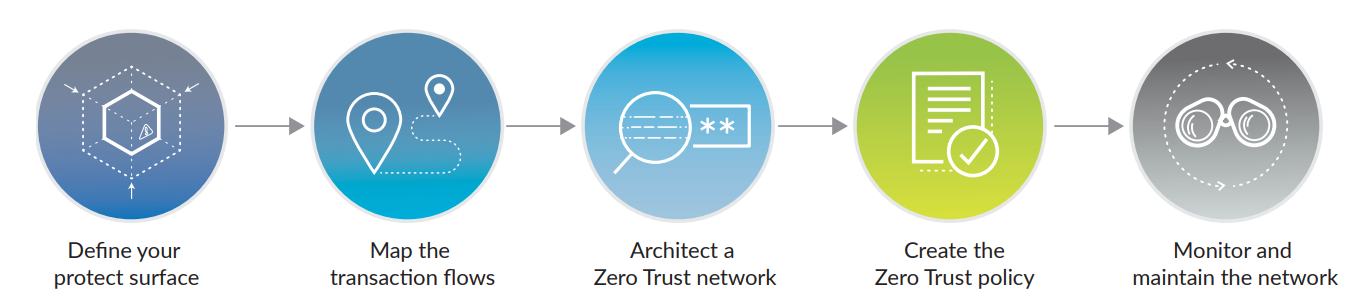
The five-step methodology
- Define the protect surface. Identifying business-critical data, applications, assets and services which are essential for operations to be protected. This is a lot easier than trying to define every aspect of the network.
- Map the transaction flows. Gain a complete understanding of how data flows and services relate to each other. Then create strong enforcement controls and policies to protect data.
- Architect a Zero Trust network. Build-in zero trust with tools such as next-generation firewalls to segment and protect the surface through layers of inspection and access control.
- Create the Zero Trust policy. Use the who, what, when, where, why, and how method to create rules that allow access only to applications and users that need it.
- Monitor and maintain the network. Learn where the gaps are in the network from Layer 1 to 7 and create updated rules to protect the surface, identify shadow IT, and malicious use.
The benefits of zero trust
In an age of big data and rapid adoption of new cloud services, zero trust helps reduce the threat surface that the business needs to protect.
Zero trust dashboards increase the visibility for IT security into all users and their activity, while the authority of authentication maintains security.
Zero trust protects against both internal and external threats. Being able to dynamically change trust (workers who have left the business, new clients in need of access), means security and monitoring remain consistent, yet flexible, across users and devices as the business changes.
A key benefit is the ability of zero trust to limit an attacker’s ability to move laterally. Say a hacker gains someone’s email password or finds a remote exploit. They might be able to access that service, but nothing else due to wider enforcement and authentication. Zero trust also reduces the risk of files being copied off the network (data exfiltration).
Finally, zero trust creates an improved security posture for businesses using either/both on-premises or cloud services. It grows as the business does, as the protect surface expands and new rules protect changing operational needs.
Getting started with zero trust security
As a relatively new concept in IT security, various approaches are being delivered by providers, while some firms are happy to build their own bespoke zero trust services. As far as maturity goes, it is hard to look beyond the Prisma Cloud application from Palo Alto, since they hired the man who founded the concept.
By simplifying the approach through a single user experience and agent across AWS, Azure and other platforms, with simple pricing, Prisma Cloud reduces the pressure on IT teams that more complex approaches will take, and is as flexible as your business needs.
As remote work, cloud services and other trends continue to dominate business operations, most IT will be focused on delivering those and should adopt a confident approach to security without the complexity.

Starting your zero trust journey
- As with most enterprise digital projects, create a zero trust center for excellence (CoE) that puts the right people and knowledge at the heart of the matter. Building a cross-functional team, including IT, security and data users will help identify the route to success and win support from business leaders.
- Educate the whole business with workshops that explain the benefits of zero trust, what changes it will bring and what they mean to everyone, demystifying what can be a strange concept to many.
- Make the first steps low-risk, quick wins, that demonstrate the zero trust approach, helping build experience and knowledge for the CoE. Show off the results that highlight added security and improved efficiency for the business.
